Cybercriminals Use NFC Relay to Turn Stolen Credit Cards into Cash without a PIN
ThreatFabric has identified a new cash-out tactic that wasn’t seen before called “Ghost Tap”, which cybercriminals use to exploit stolen credit card details linked to mobile payment services like Google Pay and Apple Pay. This method involves relaying NFC (Near Field Communication) traffic to perform transactions anonymously and on a larger scale. Cybercriminals use tools like NFCGate to relay NFC traffic between a device with the stolen card and a point-of-sale terminal, allowing them to make purchases without being physically present at the location. This tactic poses significant challenges for financial institutions in detecting and preventing such fraudulent activities. I have explained how it works and demonstrated NFC relay from Google Wallet app in the video below.
How it works
This technique introduces several new elements that make it particularly concerning:- Steal credit card details: Threat actor steals credit card information from a victim and intercepts OPT codes by using an Android malware that needs to be already installed on victim device or using phishing.
- Enroll credit card: Attacker enrolls stolen card with its own smartphone using a Google Wallet or Apple Pay application.
- Avoid detection: To obfuscate location and identity of the threat actor from law enforcement, they use mules and NFC traffic relay.
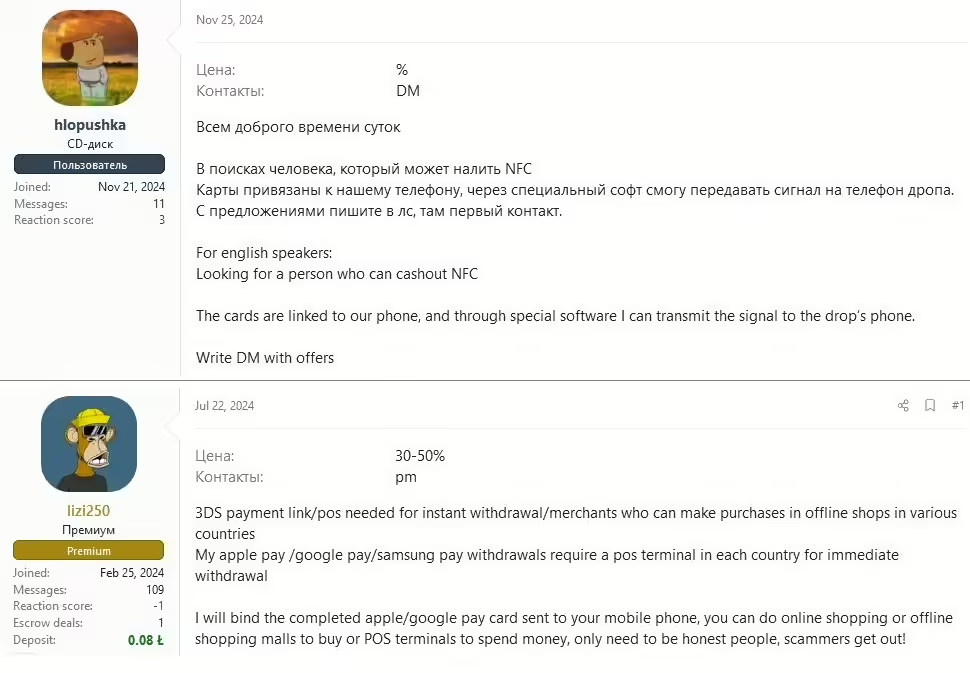
- Using mules: Using intermediaries (mules) they carry out parts of their operations, such as cashing out from stolen cards to further distance themselves from the crime. The mule can be on the other side of the world but connected to internet. In the picture below you can see posts from underground forum where threat actors are looking for mules.
- NFC Relay Attack: Unlike traditional methods, Ghost Tap uses relay attacks to exploit stolen credit card details. This allows fraudsters to perform transactions without having the physical card or being near the point-of-sale terminal.
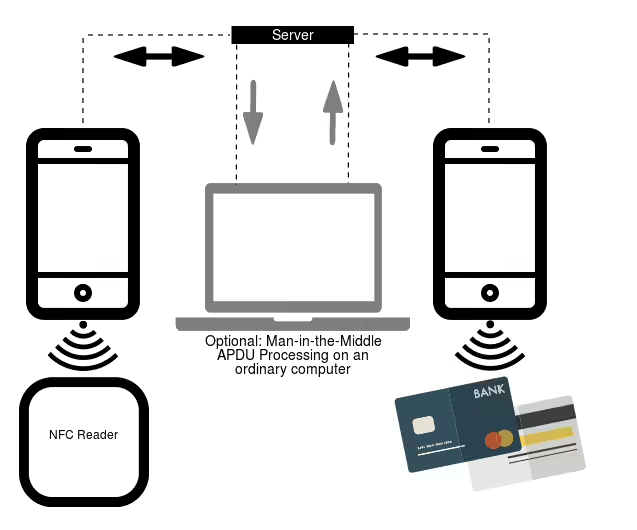
- NFCGate: To be able to relay NFC traffic from threat actor that enrolled stolen credit card information to a mule that can make payments at terminal, they used a NFCGate toolkit that can forward NFC session from threat actor device to a mule repeatedly, see the NFCGate architecture below.
- Buy goods or cash back: Mule can make unauthorized purchase at the terminal on the other side of the world for good and possibly get cash back if possible.
Bypass PIN verification: Cash-out difference between stolen physical card and card enrolled with mobile wallet app
In summary, with stolen physical payment card it is possible to make small contactless payments that are limited by the bank. Anything above this threshold, requires a PIN to enter.Payment card enrolled in wallet app on threat actor device doesn’t request to enter a PIN for contactless payments above the threshold as part of authorization, rather only authorization of device owner is necessary instead of card holder. Because of that, this type of attack effectively bypasses limit for contactless payments without knowing a PIN.
